
ZTAG Series Zero Trust Access Gateway
Secure Access Built on Zero Trust Principles
- Secure access to on-prem, cloud, and hybrid applications
- Granular, least-privilege access controls
- Strong authentication (MFA, SSO integration)
- Encrypted connections with no direct network exposure
- Centralized policy management and monitoring
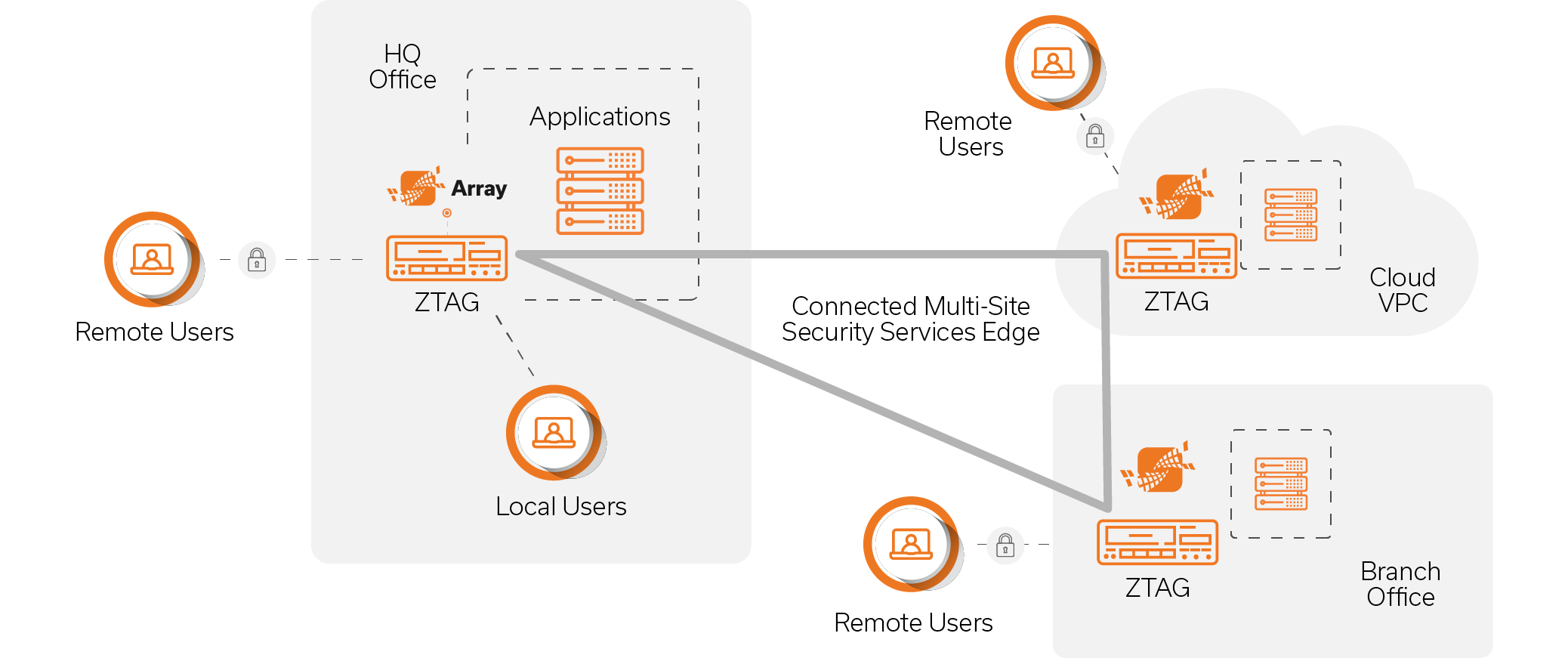
A New Perimeter Emerges
Array’s Zero Trust Access Gateway (ZTAG) creates a new security perimeter that gives users access to productivity-enhancing applications while adhering to zero trust principles. Next-gen zero trust goes beyond traditional VPNs to provide identity-based, per-app access, multi-factor authentication, continuous device posture assessment, adaptive access policies, and the ability to make internet-facing applications invisible to unauthorized users.
Available on-prem and in the cloud, Array’s ZTAG is ideal for creating connected, multi-site architectures that combine connectivity with advanced cybersecurity to provide defense-in-depth for employee and partner access. Key use cases include secure remote access, zero trust access for all users local and remote, and the creation of a hybrid cloud security services edge that spans geographically disbursed operations.
ZTAG Series Products
Secure Access Built on Zero Trust Principles
Array’s ZTAG is built on the "never trust, always verify" principle, providing workers with the resources needed to do their job, while continuously verifying every session to prevent unauthorized access and data breaches.
Advanced ZTAG Features
![]()
Single Packet Authorization (SPA)
SPA makes Array’s ZTAG invisible to network scans and unauthorized users, preventing brute force hacking and DDoS attacks.
![]()
User Identity & Device Validation
MFA, SSO and HW ID support a range of AAA protocols, IdP providers, as well as device certificates and fingerprinting.
![]()
Continuous Adaptive Access Control
ZTAG’s built-in policy engine continuously recalculates user access rights based on changing risk factors.
![]()
Advanced Client Security
Restricts clipboard access, blocks screen sharing, and disables file uploads and downloads in sensitive sessions.
![]()
Granular Authentication Parameters
Validate OS and patch version, antivirus, port use, IP reputation, and connection type as prerequisites for authentication.
![]()
Least Privilege Application Publishing
Layer-7, Layer-4, and Layer-3 app publishing shrinks the attack surface by providing access on a per user, per resource basis.
![]()
End-to-End Encryption
User and gateway connections use the latest TLS and IPSec encryption protocols and ciphers, including WireGuard VPN.
![]()
Reporting & Monitoring
Records all access activities, and allows logs to be queried by date, user, application, IP address, and other parameters.
Key Use Cases
![]()
Secure Remote Access
Remote workers cannot directly access internal resources. For these employees, ZTAG securely proxies internal services in a simple, scalable manner.
![]()
Zero Trust Secure Access
Front-ending business-critical apps with ZTAG, enterprises can enforce zero trust access control policies for all users, whether local or remote.
![]()
Security Services Edge
ZTAG can be deployed on-prem and in the cloud to create a security services edge to which additional security can be layered to protect sensitive data.

